An improbable route took William F. Friedman from the study of plant genetics to a reputation as father of U.S. cryptology—one that made a huge impact on the war.
DURING THE U.S. CONGRESSIONAL investigation of the Pearl Harbor attack held immediately after the war, a stunning fact emerged: even before the attack, American cryptologists had mastered the Japanese cipher machine they had codenamed “Purple” and had been reading the most secret Japanese diplomatic communications. The open irony of this disclosure was that since Japanese diplomats had been kept in the dark about their government’s intentions, they did not reveal the planned attack. The concealed irony was that the Japanese communications disclosed far more than Japanese secrets.
Nearly 30 years transpired before a groundbreaking book, F. W. Winterbotham’s The Ultra Secret (1974), revealed the vast triumph of Allied codebreakers against German secret communications, most famously the German Enigma machine. Since then, the declassification of thousands of documents detailing Allied success against coded Axis communications has generated shelves of works celebrating these accomplishments.
That mass of literature hints at a huge reciprocal question: just how secure were Allied secret communications? During the decades after the war, disclosures divulged some Axis success, perhaps most notably German penetration of the code used through 1943 to route Allied convoys. That such disclosures are rare, though, points to a vital Allied supremacy in communications security—yet no great library elaborates on this crucial achievement. What has emerged from that void is that behind the two most significant American cryptography achievements—the codebreaking success against the sophisticated Japanese Purple cipher machine and the development of the most secure cipher machine of the war, the United States’ SIGABA—was the same man, William F. Friedman, in parallel stories that unwind along a train of improbable coincidences and bizarre twists.
FIRST, SOME KEY TERMINOLOGY. The term “codebreaking” is often loosely applied to decrypting both codes and ciphers, but these are two very different categories. Take, for example, the word “battleship”—which in the world of codebreakers is termed “plain text.” In a code, typically there would be a specific multiple-letter or numerical sequence standing for “battleship,” like “ABCDE” or “12345.” A cipher, on the other hand, involves disguising not the word as a whole, but each individual letter. In a typical World War II cipher system, when a code clerk typed the first letter of the word on a keyboard, the letter “b”—through a series of electrical and mechanical connections—would come out enciphered in the form in which it was to be transmitted: the letter “w,” perhaps. On each subsequent occasion on which “b” is typed, a different letter—say an “e,” then a “m”—would emerge as the enciphered text, and so on through a vast number of variables. Thus, when encoded, “battleship” comes out as, say, “ABCDE”—but when enciphered becomes, perhaps, “WGEXVIMQZO.” Strictly speaking, Purple and Enigma were cipher, not coding, machines.
ONE OF THE STORY’S most bizarre twists comes at its very beginning, when William Friedman got his introduction to codebreaking thanks, in a roundabout way, to William Shakespeare. Of course, since Shakespeare died more than 300 years earlier, his role requires a bit of explanation.
In the early 20th century, a man whom author Liza Mundy describes as a “hyperactive, wild-eyed person of myriad scientific enthusiasms and no scientific training,” George Fabyan, poured an inherited fortune in textiles into a private research think tank, Riverbank Laboratories. Set on a meticulously maintained estate in Geneva, Illinois, it was a place as quirky as its owner, featuring a Dutch windmill and Roman-style bath.
In 1915, to pursue one of his scientific enthusiasms, Fabyan hired a recent graduate of Cornell University with a degree in genetics, the dark-haired and dapper William Friedman, 24. Friedman’s task was to figure out how to improve wheat crops.
But Fabyan’s true obsession was proving that the author of Shakespeare’s plays was a contemporary, Sir Francis Bacon—a popular conceit at the time. Fabyan believed Bacon had installed coded messages in the texts to establish his authorship. To pursue this pet project, in 1916 Fabyan hired Elizebeth Smith, 23, a vivacious, multi-talented young woman with a degree in English and an interest in Shakespeare. Friedman became intrigued with Smith and she with him, and a relationship began. Both soon shared a rapidly deepening interest in codes and ciphers—as well as complete scorn for Fabyan’s Bacon obsession.


Fabyan’s plunge into codes and ciphers improbably transformed Riverbank Laboratories into the launch pad for American cryptographic efforts in World War I, with starring roles for the newly married William and Elizebeth. Based on his wartime work, in 1921 William became the first full-time civilian employee of the U.S. Army working on cryptographic matters—all that involves making and breaking of codes and ciphers. Elizebeth went on to her own very distinguished career as a codebreaker, notably against rum-running bootleggers and, later, against Nazi agents in South America.
William and Elizebeth had entered the arcane world of codebreaking at the same time that ancient enterprise was making a dramatic advance. For centuries codes and ciphers had typically relied on hand-worked, paper-based systems. There were also a smattering of crude mechanical ciphering devices—discs, for example, composed of two wheels that could be rotated to align the “plain text” letter on one wheel with a different letter in an adjacent position on the other. But as technological innovations accelerated the tempo of military operations, automated cipher machines seemed essential to speed coded communications. By the 1920s an electromechanical cipher machine had become technically feasible.
In such a system, the machine operator worked on a keyboard. Each keystroke initiated an electrical impulse that streaked down circuits variously channeled through mechanical devices like rotors. These rotors had multiple internal wiring connections or switches to scramble the path of the impulse, creating thousands of variables between the “plain text” letter that was struck and the enciphered letter that came out. The term for this process was “stepping,” and it determined just how secure—or insecure—the system was.
When various inventors presented their cipher machines to the U.S. Army Signal Corps, it referred the devices to Friedman—who found even the most complex machines wanting. To determine the machines’ security, Friedman devised ingenious mathematical methods of divining the relationship of the enciphered text with the underlying plain text.
With the creation of the army’s Signal Intelligence Service in 1929, Friedman, appointed its chief, was able to hire three assistants in April 1930—Frank B. Rowlett, Abraham Sinkov, and Solomon Kullback. Friedman trained his new team to apply his insights.

But Friedman recognized that cryptographic security was a two-way street. While penetrating enemy ciphers and codes represented a huge advantage, it was just as vital to protect American secret communications. So in the early 1930s Friedman invented a high-speed but extremely secure cipher machine. In 1935, Rowlett—then 26 and Friedman’s team leader—expanded on Friedman’s work with an inspired idea for stepping that offered unmatched security. In essence, where one input of electric charge produced one output in Friedman’s machine, Rowlett devised a means of having a single input produce up to four outputs. That exponentially increased the randomness of the stepping.
The story then takes a turn that mimics the wild permutations of the cipher machine. The army was already invested in prototypes of cipher machines based on Friedman’s early designs and refused to incorporate Rowlett’s breakthrough. Stymied by his own service branch, Friedman met with a U.S. Navy cryptologist, Lieutenant Joseph N. Wenger, in October 1935. Although the army and navy had not then been closely cooperating in cryptographic enterprises, after Wenger expressed his dissatisfaction with the navy’s first-generation cipher machine—the Electric Code Machine Mark I, or ECM I—Friedman disclosed his innovations and Rowlett’s dramatic upgrade.
Wenger and his colleagues proceeded to apply these concepts in developing a new machine, but because the army had had some of Friedman’s key papers published at the completely open Government Printing Office—something the navy saw as a gross security violation—they told Friedman and the army nothing about their efforts. Consequently, Friedman heard no more until he was summoned to a meeting at the Navy Building on February 3, 1940. There, navy officers unveiled what they called the Electric Code Machine Mark II (ECM II). This device was basically Friedman’s design with Rowlett’s innovation.
Both services agreed to adopt the new machine, which in army nomenclature was known as “Converter M-134-C,” or by the pithier (and largely nonsensical) name, SIGABA. Production models of the machine began rolling off assembly lines in March 1941 and its use continued into the Cold War. No foreign nation, so far as is known, has ever broken this cipher machine.


THE CODEBREAKING UNIT Friedman created for the army had from its inception focused primarily on the cryptographic efforts of the Japanese, then regarded as the greatest potential threat to the U.S. By applying Friedman’s methods, they had since 1936 been able to read diplomatic messages sent on what the Japanese called the “A Type” cipher machine, which the Americans had dubbed “Red.” In late 1938 American cryptanalysts began picking up references to a pending change to a “B Type” machine. And on February 20, 1939, diplomats at 11 key Japanese embassies, including that in Washington, D.C., transitioned to the new machine—one immortalized in the history of codebreaking by its American code name: “Purple.”
Like Red, the B Type machine worked on the 26-letter Roman alphabet. (The use of the Roman alphabet may seem odd, but it was vastly less complex than written Japanese, and thus reduced the internal complexity and, therefore, size of the machine; it also made the transmission of coded diplomatic messages over commercial international cable systems cheaper because the text was shorter.) Initial analysis demonstrated the markedly higher frequency of six letters, which appeared to parallel the same characteristic of the Red machine, where the six letters were discovered to be vowels (A, E, I, O, U, and Y).
Further study, however, indicated the new machine was no mere modification of Red. It turned out that the new machine ran on a cycle through 25 “alphabets.” Each of these alphabets was scrambled differently, but the sequence of the 25 alphabets remained the same. Furthermore, each message being sent had its own key—a snippet of text called an “indicator”—which informed operators of the starting point for a message among these 25 alphabets. Using tested techniques, just under two months after the B Type machine came into use the codebreakers could ferret out the vowels in any lengthy message. They deduced that although there were 25 starting points—one for each scrambled alphabet—the Japanese employed 120 indicators to disguise those starting points.
When what the codebreakers called the “6s”—the vowels—popped out from decipherment, they formed skeletons of words or phrases in the plain text. Astute deductions based on the vowels and their context could then sometimes fill in the spaces between them. For example:
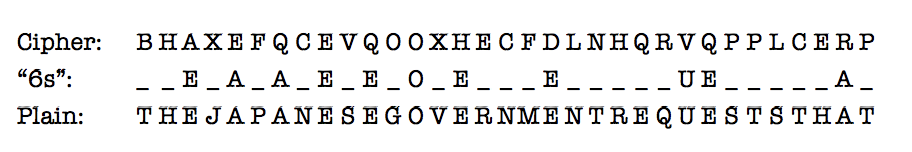
The greater challenge of ferreting out the “20s”—the consonants—remained. An underlying plain text of a document that was intended to be delivered in English, as in the example above, greatly facilitated the work of the codebreakers. This was both because virtually none of the codebreakers understood Japanese and because the few translators available could spare little time for this work. But if the job of the codebreakers increased tremendously when the “plain text” was in Japanese—as it usually was—the difficulty zoomed to staggering complexity on May 1, 1939, when the Japanese adapted a version of what was called the “Phillips Code.” The Phillips Code was a method of shortening the length of commercial telegrams, thereby reducing their costs. As applied here, it comprised a lengthy series of arbitrary letters and abbreviations standing for numbers, punctuation marks, words, syllables, and sometimes phrases. It produced this sort of “plain text” at the beginning of a message:
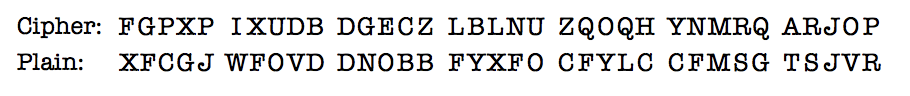
Thanks to the Phillips Code technique, “plain text” in this example emerges as gibberish that actually means: “Number 15 (part 1 of 2 parts) Secret, to be kept within the Department paragraph On March 16th the American Ambassador Grew….”
The longer the Americans worked, the more apparent it became that the new B Type machine did not work on cyclically repeating cipher sequences like those produced by the revolving rotors typical of cipher machines at that time, including Red. Friedman’s report of October 14, 1940, “Preliminary Historical Report on the Solution of the ‘B’ Machine,” was tightlipped on exactly how his unit surmounted all the devilish obstacles the machine’s design presented. Read carefully, though, the report acknowledged that the codebreakers had managed to decipher a set of a mere six messages, all in one indicator or converted to that indicator. Just two of the messages were complete or near-complete; the remaining four were fragments.
From this minuscule sample the codebreakers finally discerned brief and scattered intervals of repeated sequences. It was September 20, 1940—19 months to the day from the B Type machine’s introduction.
As team leader Rowlett gathered in conversation with a couple of cryptanalysts—part of the expanded staffing in the late 1930s—another added staff member, Genevieve “Gene” Grotjan, stepped forward. Grotjan, 27, had graduated summa cum laude with a degree in mathematics from SUNY Buffalo—but, being a woman, had not been able to secure a job at a college mathematics department. She was working as a lowly statistical clerk calculating pensions for the Railroad Retirement Fund when Friedman hired her as a junior cryptanalyst in October 1939.
“I have something to show you,” Grotjan told the others.
In a moment of insight that Grotjan could never fully explain, as she had conducted yet another tedious examination of worksheets on Purple messages, she could suddenly see multiple locations that revealed correlations between plain text and the cipher text equivalents of consonants. Excitedly she directed the attention of Rowlett and the others to four areas she had circled on the worksheets. Her fellow cryptanalysts instantly grasped the monumental significance of her finding, which cracked open a previously sealed doorway that might well lead to full access to the original text.

With his arms upraised and clasped like a victorious prizefighter, fellow cryptanalyst Albert Small began a jig around Grotjan’s desk and exclaimed, “Whoopee!” The normally sedate Robert Ferner shouted, “Hurrah, hurrah!” as he clapped his hands. And Rowlett began jumping up and down and letting loose with cries of, “That’s it! That’s it! Gene has found what we’ve been looking for!”
In a classic understatement, William Friedman noted, “There was much excitement at this first glimmer of light upon a subject that had for so many months been shrouded in complete darkness and regarded occasionally with some discouragement.” It was a sublime moment, one demanding that the normally restraining traces of bureaucratic dignity be released in exuberant celebration. So the codebreakers—with Friedman’s approval—kicked up their collective heels and ordered Coca-Colas all around.
EVEN WITH THESE FIRST CLUES of some cyclic or symmetric sequences, the underlying basic cryptographic laws that would explain the shifts from one sequence to another at first defied solution. But the reenergized team accelerated its tempo with much night work so that just one week later, they could hand in two translations of fresh messages representing the very first solution of the Purple machine. The date was September 27, 1940—stunningly the very day Germany, Italy, and Japan sealed their alliance under the Tripartite Pact. The coincidence of the Axis powers uniting on the same day that American cryptologists cracked the Japanese cipher system that would go on to betray the alliance’s vital wartime secrets would be rejected by even the most imaginative novelist as beyond belief.
Having identified one indicator, the next phase involved not only the solution of the remaining 119 indicators but also the transformation of the theoretical principles of structure and operation of the machine into the construction of an actual operating B Type machine. Their Purple machine analog consisted of 13 rotary, 6-level, 25-point switches of the type called “stepping switches” employed in automatic telephone systems. One of the 13 switches controlled the encipherment of the vowels and advanced through the same 25-point cycle repeatedly, as often as was required to complete the message. Three banks of four switches each enciphered the consonants, with each bank having 500 cross-connections, making a total of 1,500 sub-circuits available for enciphering any given letter. That Friedman’s team did this without ever having seen an actual Purple machine makes the accomplishment all the more remarkable.


IN ONE OF THE GREAT IRONIES of the war, Japanese diplomatic codes divulged invaluable intelligence not just about Japan’s plans and intentions but also about those of Germany. Adolf Hitler periodically tendered his strategic plans as well as information about secret German technological developments to the Japanese ambassador in Berlin, Hiroshi Oshima. On one memorable occasion in late 1943, Oshima reported in great detail on the guided tour the Germans had provided him of their Atlantic coast defenses, including those at Normandy. Other members of Japan’s diplomatic corps in Germany also communicated valuable intelligence to Tokyo. And since most of these messages were sent via the B Type machine whose code the Allies were now reading, they also delivered this top-level German intelligence to the Allies. (Other important intelligence flowed from breaks into the additional cipher and code systems used by Japanese naval and military attachés in Germany; Allied codebreakers had targeted these, too, with success.)
The Allies likely would have known little of that had a potential catastrophe in Singapore in early 1942 not played out in their favor. In response to a request from the main British codebreaking station in the Far East—the Far East Combined Bureau—the Government Code and Cipher School in England had shipped one of the precious Purple analogs the United States had supplied them to Singapore. The machine arrived in late December 1941 when the Japanese were already advancing down the Malayan Peninsula toward Singapore. When the Japanese neared Singapore, the bureau fled the island for Ceylon (now Sri Lanka) on January 5, 1942—without the device. The fate of the machine remains unknown. Presumably it was destroyed in the chaotic final days before Singapore surrendered to the Japanese on February 15, 1942, or it passed undiscovered—or perhaps unrecognized—by the Japanese.


The potential fallout from a Japanese capture of this machine is breathtaking. Discovery that the Allies had not merely penetrated secret communications but had recreated sight unseen Japan’s most sophisticated cipher machine would have stunned all Axis communications security organizations, unmasking a capability that would demand a vast upgrade. Much of Allied success against the German Enigma and other purportedly secure communications methods hinged on careless errors in security practices founded on a blasé confidence in the impenetrability of those systems. A captured Purple machine would have shattered that illusion.
An overall upgrade of Axis communications security methods might well have defeated or at least severely curbed the Allied success in this arena—which British historian and cryptanalyst F. H. Hinsley believed shortened the war by three years. It potentially also could have affected the willingness of American codebreakers to collaborate with their British counterparts. That alone would have retarded Allied efforts against Axis communications with incalculable results.
BEHIND THAT NEAR MISS and the two American codebreaking triumphs, though, was a sadness. While William F. Friedman’s Signal Intelligence Service continued to innovate and prosper, Friedman did not. The incredible stresses Friedman had been under through the 1930s—and the still-greater strain in penetrating Purple—broke him. On January 4, 1941, he began a three-month treatment at Walter Reed Hospital in Bethesda, Maryland, for what was classified as a mental breakdown. Afterward he was ostensibly promoted as the Signal Intelligence Service’s director of research. In reality, though, he was relegated to the much less important role of technical adviser. But his brilliant insights, as well as the open, collegial atmosphere Friedman fostered, remained stamped on army codebreaking operations.
Friedman retired in 1956 and, with Elizebeth, returned to the subject that brought them together: disproving the notion that Sir Francis Bacon had embedded code in Shakespeare’s plays. Friedman died in 1969 and is buried at Arlington National Cemetery. On his tombstone is a phrase attributed to Bacon: “Knowledge is power.” ✯

This article was published in the June 2020 issue of World War II.





